Our safety auditing usually focuses on harms created by unmonitored data supplies and harmful UX design patterns. However, during our K12 edtech research last year, we observed unique harms of dangling domains and decided to act. Dangling domains have not (for whatever reason) been renewed by the previous owner and are available (or soon-to-become available) for purchase. Dangling domains are often opportunistically purchased by bad actors who install malicious sites at the abandoned domains. This is referred to as “hijacked domains.” To our dismay, we observed such hijacking several times in our deeper dive exploring the use of WebView in K12 edtech.
Also, in our research last year we found a widely used SDK’s domain available for purchase that, if hijacked, would have potentially put millions of Apple device users at risk. As we described in our post, Apple ultimately purchased this dangling domain due to our urging. After missing the window to buy some dangling domains that were later hijacked, we resolved to be more proactive.
What are Dangling Domains
When a business or organization fails to renew its domain name registration (typically once per year), the domain can become available for outside buyers to purchase, as shown by this chart provided by ICANN

Source: ICANN
Education and government organizations routinely switch to .edu or .gov domain names, creating regular risk scenarios. While these changes are healthy in the long run, they leave behind previously legitimate domains in disuse. The organization will often allow their old domain name to expire, making it available for purchase by anyone, including malicious actors.
We Built a Tool to Continually Monitor for Dangling Domains
After confirmation from the US Department of Homeland Security that no one in the federal government is accountable for monitoring dangling domains (outside of the .gov top level domain), we decided to develop a monitoring tool to identify soon-to-be dangling domains. We prioritized this category because fresh expiration is attractive to hijackers looking for domains that have been in use recently.
Tens of thousands of domains drop daily, so manually sifting through them to find names that previously belonged to legitimate organizations is far from feasible. To make it possible, we created a tool that uses keywords to filter through the thousands of domains and then analyzes the references to each domain of interest.
Because it wouldn’t be feasible to try to catch every legitimate dropping domain, we decided to focus our efforts on education and government domains (except for .gov domains). Within this category, we prioritized domains that were referenced in websites in .gov and .edu domains, and in Wikipedia and Facebook. References on controlled top-level domains (like .edu) indicate trust, so these domains have the highest potential to be abused by scammers.
What We’ve Found
Since we started monitoring a couple of months ago, we’ve identified and secured 13 domains that were previously associated with government and academic organizations (see Table 1). Although some of these domains belong to organizations that no longer exist, we are in the process of transferring the domains to their legitimate owners where possible.
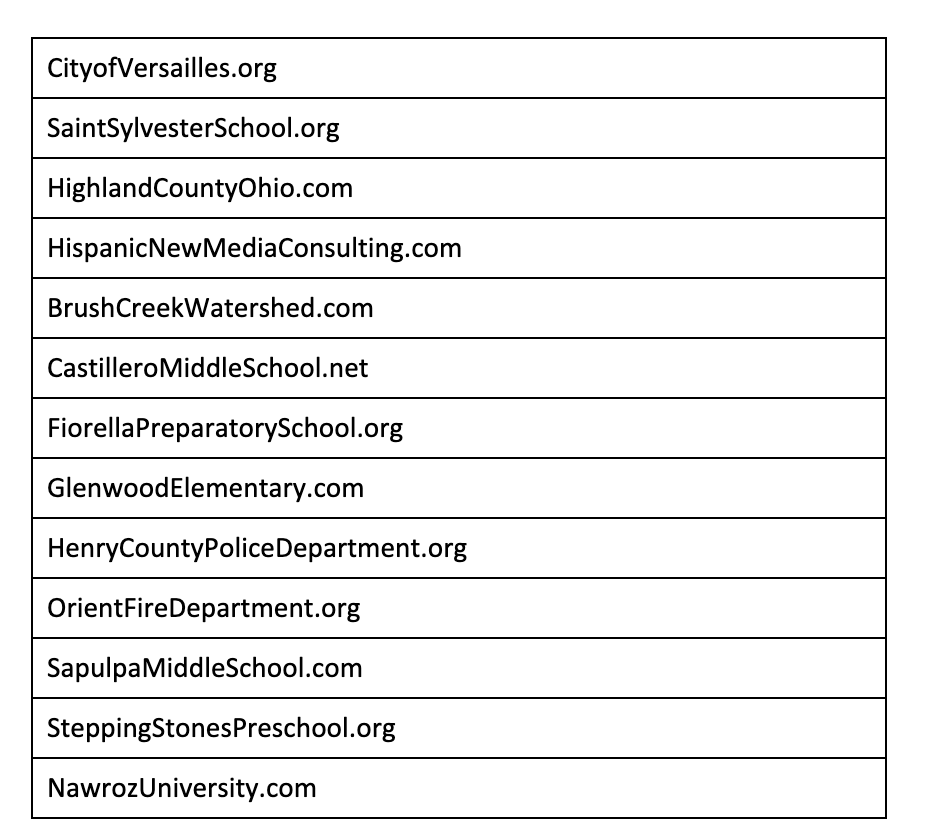
Table 1: Purchased Dangling Domains
Unfortunately, we weren’t always able to secure the domains we identified as possible targets for hijackers. Some higher-profile domain names were more expensive than our budget allows.
This was the case for IraqiGovernment.org, a domain used by the government of Iraq in the mid-2000s. After this domain dropped, a three-day bidding war on dropcatch.com ensued, with bids quickly reaching hundreds of dollars. Less than a week after the domain fell under its new owner, it was being used to host Indonesian gambling advertisements (Figure 1).

Figure 1: Hijacked domain, IraqiGovernment.org
Sadly, this outcome is all too common. Nearly every domain name we couldn’t secure has been hijacked by bad actors, e.g. spammers, malware distributors, or people aiming to resell the domain to those groups. These sites could now advertise anything from sports, to drugs, to pornography.
We also caught TheWhiteHouseProject.com, a domain used by a now-dissolved women’s advocacy group, in the middle of the hijacking process (Figure 2).
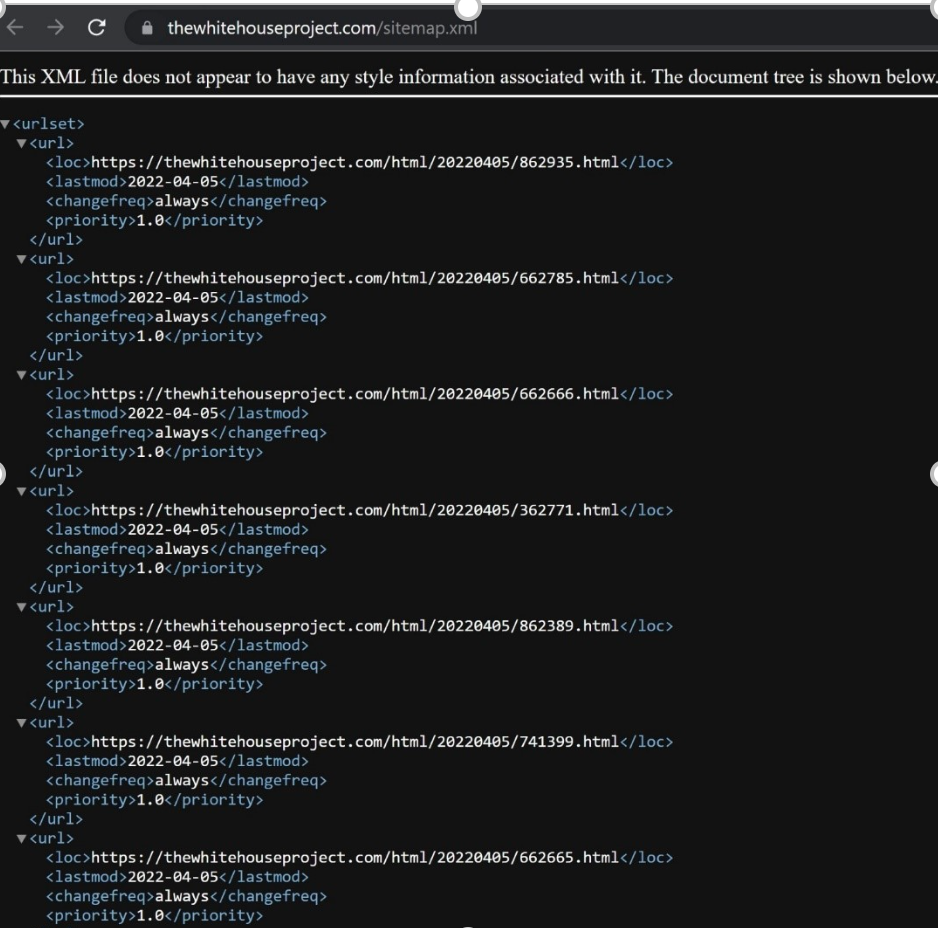
Figure 2: Hijacked domain, TheWhitehouseProject.com
The above xml file is used by ad networks to redirect web traffic to the highest bidder. Shortly after it was hijacked, the domain was hosting sports advertisements. A few weeks later it was hosting pornography.
One domain we managed to secure had undergone hijacking in the past. CityOfVersailles.org was the domain name used by Versailles, Missouri. After it dropped in 2016, it became the host of a series of blogs concerning erectile dysfunction and marijuana (Figure 3).
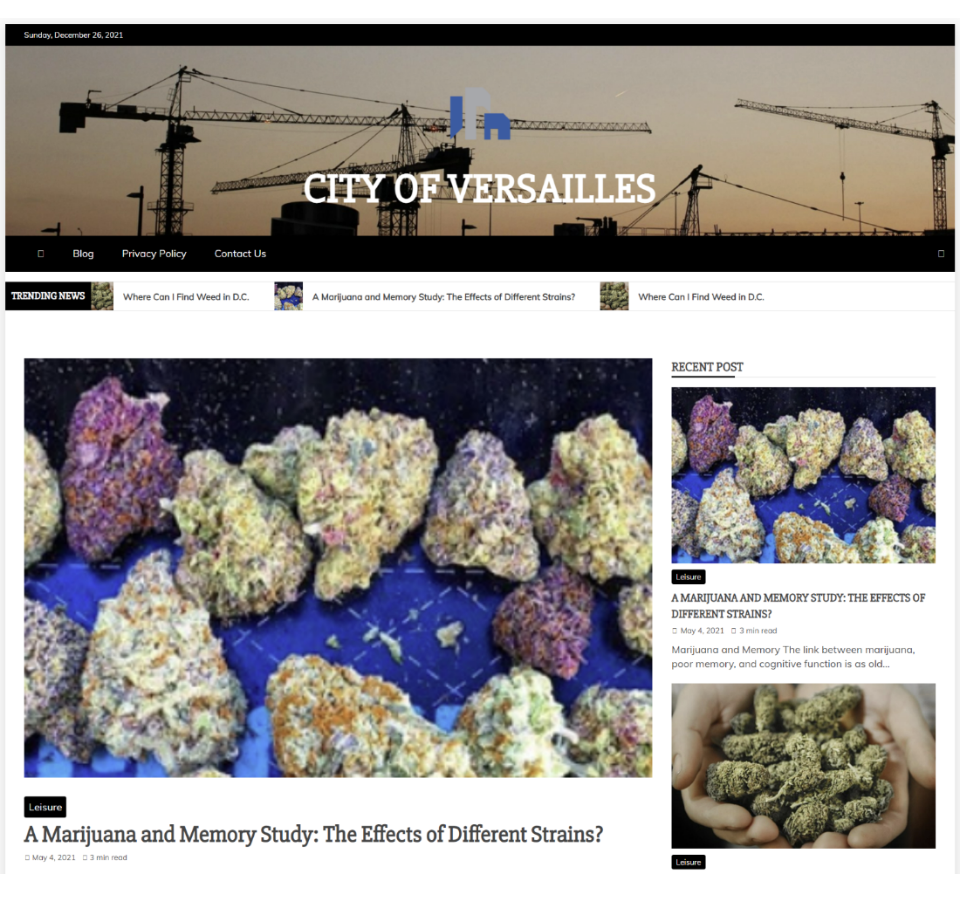
Figure 3: Hijacked domain, CityOfVersailles.org
What’s Next?
Dangling domains present massive ongoing safety harm to people, businesses, governments, and institutions. As a small startup organization, we do not have the funds to monitor and procure all the dangling domains that are at risk of hijacking. Proper monitoring and protections for dropping domains requires a well-funded organization or even a network of organizations. We hope that surfacing this ongoing serious safety risk for Me-s and B-s can catalyze policymakers and other security organizations to develop stronger protective systems. We are happy to share our methods and resources to help get a more robust solution in place.
